|
|
Legacy Information
This page shows content from our old website. It might move in the near future. To get the most up to date information, please use the navigation menu at the top.
Buy now!
Features
Uncategorized
Not yet sorted into categories.
Anti-SpywareSpybot's Anti-Spyware protection uses our unique technology to find and remove all kinds of spyware, including adware, tracking software, keyloggers and other unpopular software. Your privacy is our ultimate goal! |
Anti-VirusTo provide you with the best possible protection, we've included an award winning anti-virus engine. It's the engine of choice of the best rated anti-virus products on AV-Test and AV comparatives. And on top of that most elaborate malware protection, you get our own specialized anti-spyware engine that covers the spyware grounds beyond! |
Live ProtectionLive Protection is Spybots form of real time protection. Live protection scans and monitors all newly created and running processes on your system. Malicious processes are blocked before they start to prevent infection on your system. |
Anti-BeaconOur anti-telemetry tool Anti-Beacon Plus is available to all users of the Spybot Professional and the commercial editions. |
System ImmunizationImmunization pro-actively protects your system against malware attacks by blocking access to sites known to contain malicious or unwanted software. It also blocks tracking cookies and browser plugins that are known to contain malware. Immunization supports many popular browsers, including Internet Explorer, Opera, Firefox and Chrome. 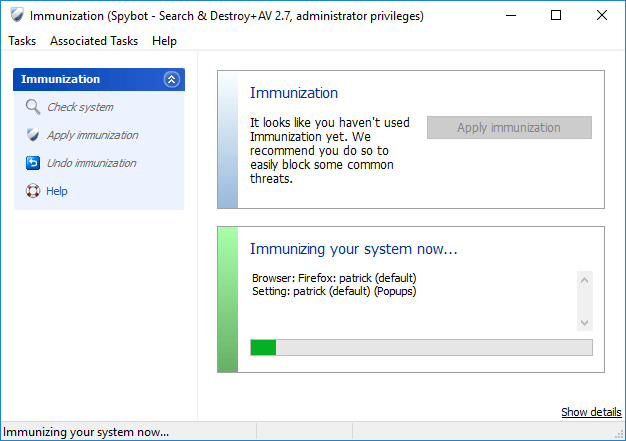 |
Startup ToolsStartup Tools allow you to manage what happens and what gets loaded at system startup. If you open this tool you will see a comprehensive set of tabs. Clicking on a tab will allow you to inspect and change the behaviour of what is loaded. This powerful tool should be used with caution as it allows you to make registry changes as well as other changes that effect your system. It can be useful if you suspect changes may have been made without your knowledge. 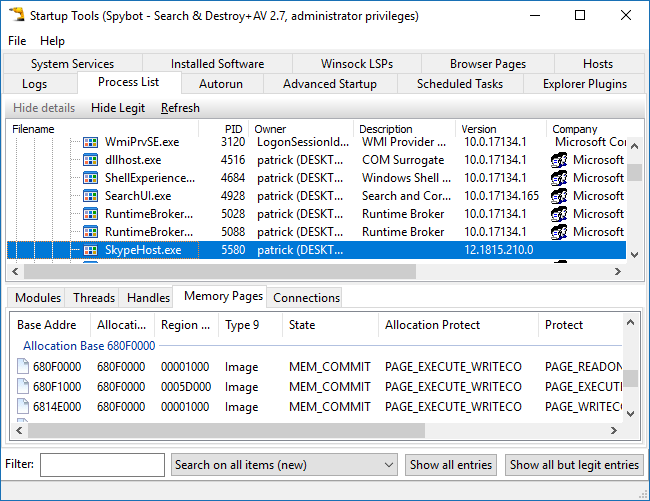 |
Rootkit ScanRootkits use technologies to hide themselves and their actions from users and other system processes. The Rootkit Scan is a special scan that can locate these rootkits. This scan includes checks of the file system, the registry and some process related lists. |
Automatic Signature UpdatesStaying up to date with all malware signatures is essential for your security. All paid editions of Spybot will download new signatures multiple times per day - automatically and in the background. 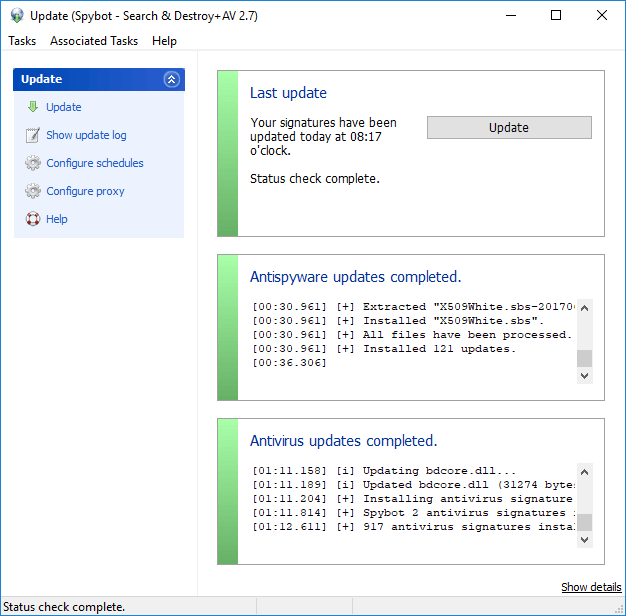 |
Task SchedulingIf you have purchased Spybot you have the advantage of being able to automate tasks. Using the Schedule option in Advanced Tools → Settings Spybot can create a Windows Scheduler task to keep your Spybot up to date, immunized and run system scans regularly. 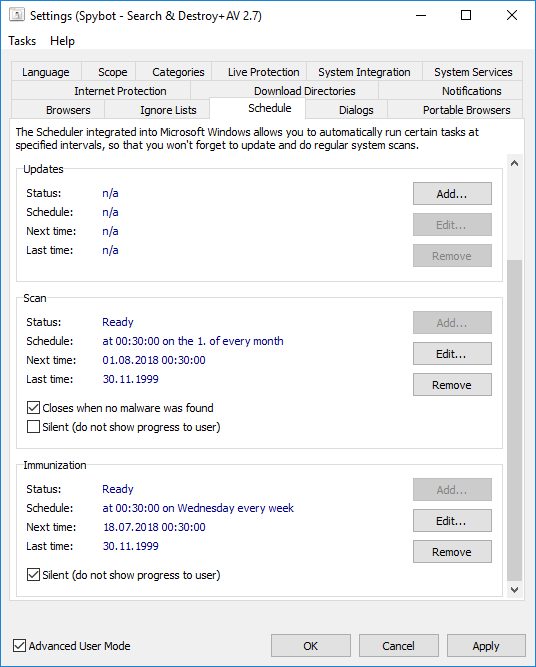 |
Protected Repair EnvironmentWhen you choose the Protected Repair Environment, a new Windows Desktop is opened and the Start Center runs in a way so that other software cannot interact with it. This prevents keyloggers and other malware taking over control of Spybot, using the same security desktop separation technology that the Windows Login screen and the User Account Control dialogs use.  |
System Registry RepairMost registry cleaner software promises to speed up your system which is not really possible. These cleaners may also come with unwanted additions such as adware or spyware. Our System Registry Repair allows you to do some basic cleanup and repair in a number of categories where changes might positively affect user experience, for instance helping Windows find misplaced Help files. It can either delete or repair broken entries by offering you you the options, for example, of locating or searching for files that have been moved. 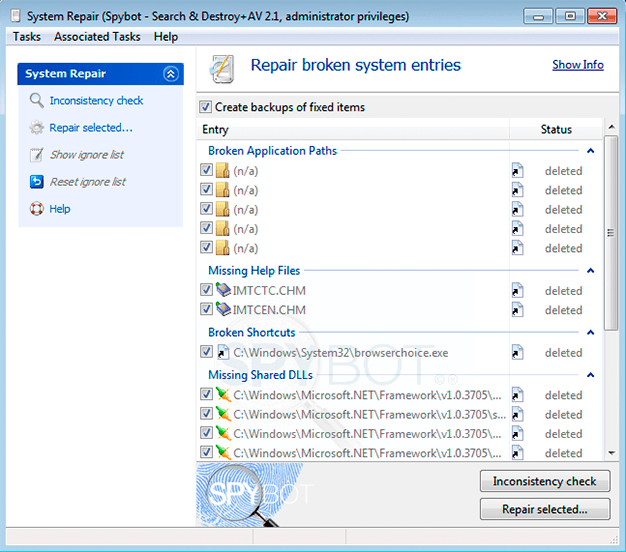 |
Priority SupportBeside the standard support options we at Safer-Networking Ltd. strive to support you in case of questions or problems. So if need help, do not hesitate to use our contact page! |
Secure ShredderThe Secure Shredder is a tool to safely remove files from magnetic hard drives. It uses multiple passes to make sure the files cannot be recovered. 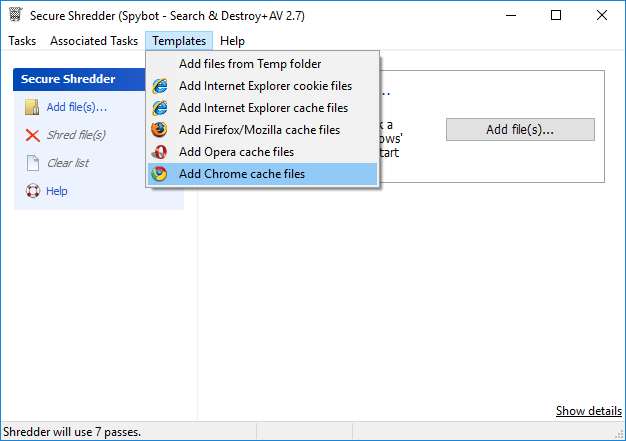 |
Script EditorIf you are familiar with a common programming language you might want to define some detection patterns yourself. Just to get rid of some unwanted files or any item you regard as malware. This is not too complex when using our OpenSBI syntax and Pascal. A simple script that you could implement using a simple .sbi file might look like this: 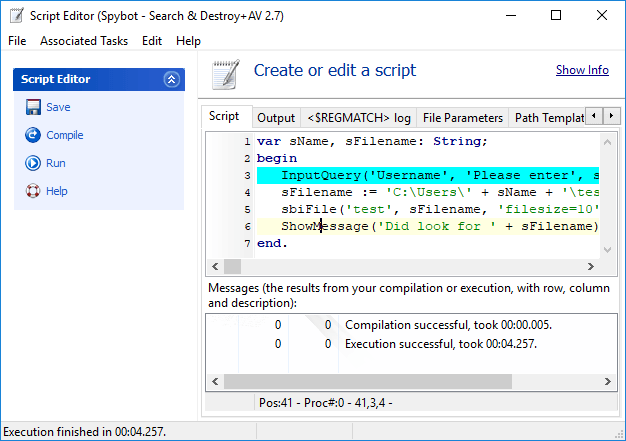 |
Command Line ToolsThe system administrator may schedule tasks and use Command Line Parameters or even Command Line Tools to perform different tasks without user interaction. Powershell Scripts or Batch Files may help and the Windows scheduler can support special tasks as well. Command Line Tools are available for:
 |
FileAlyzerFileAlyzer is a tool to analyze files. It shows basic file content, a hex viewer, and a range of customized displays for interpreted file structures. It also supports generation of OpenSBI advanced file parameters. 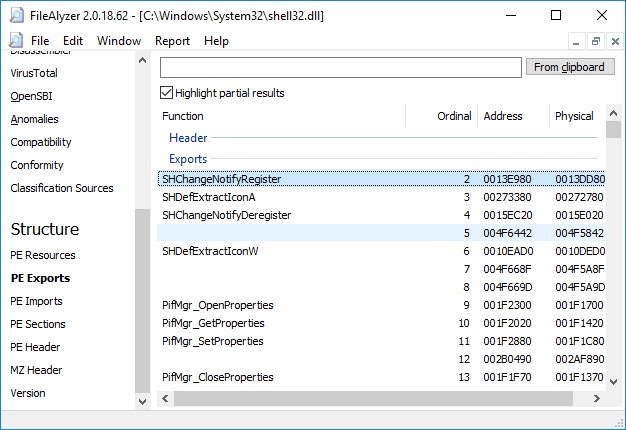 |
RegAlyzerRegAlyzer is a tool to browse and change the registry. It was created because of a few features we missed in the original regedit tool, from support for exotic value types over background and regular expression search to better bookmarks, displaying .reg files in the accustomed style and a history view. 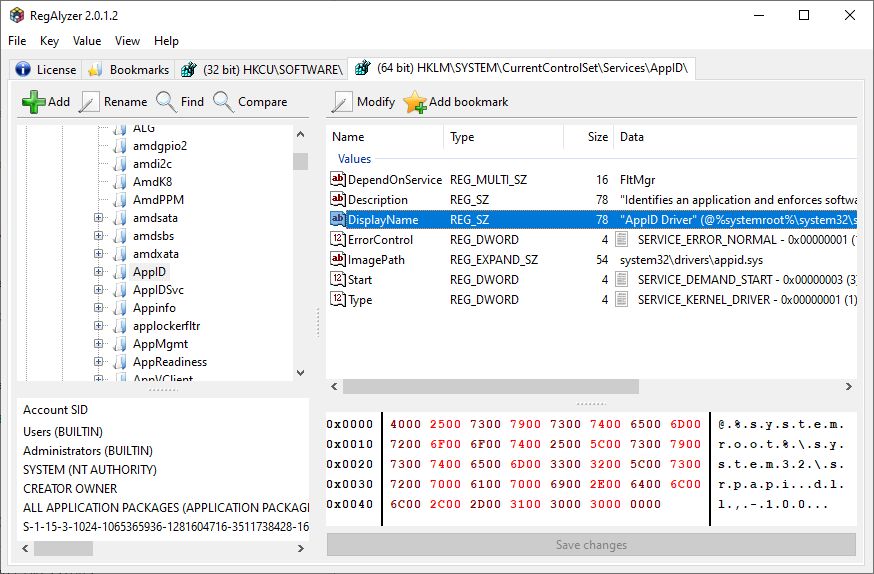 |
| One Year License |